|
|
The FBI goes to a rancher to tell him that a bank robber has crossed his property. The FBI takes the rancher to a place on his land where the prairie ends at a gorge that separates the ranch from the foothill mountains. It is a deep gorge. The FBI then asks the rancher to build a bridge across the gorge so agents can cross the gorge to see if the bank robber left any clues on the other side. How is the rancher supposed to respond? “Get the hell off my property!” would probably be the most common response. But this is exactly what the FBI wants Apple to do when it is asking the company to write a hack program to get around Apple's new iPhone encryption. |
cyberbarf VOLUME 15 NO.8 EXAMINE THE NET WAY OF LIFE MARCH, 2016 ©2016 Ski All Rights Reserved Worldwide Distributed by pindermedia.com, inc. |
|
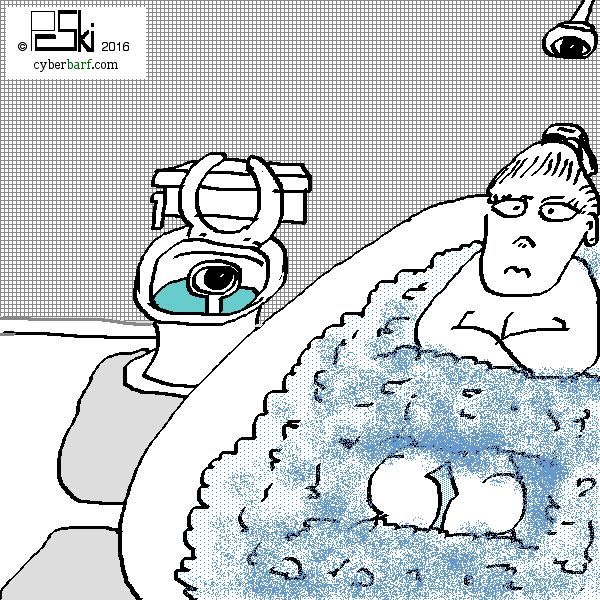
Apple has objected to the FBI court order asking it to create a back door spying tool. Privacy and security advocates fear this is the Dawn of Big Brother: unlimited government surveillance. Apple CEO Tim Cook described the government's request as “asking Apple to hack our own users and undermine decades of security advancements that protect our customers - - - including tens of millions of American citizens - - -from sophisticated hackers and cybercriminals. The same engineers who built strong encryption into the iPhone to protect our users would, ironically, be ordered to weaken those protections and make our users less safe.” The federal government unilaterally went to a court to get a judge to enter an order forcing Apple to assist the FBI in unlocking an iPhone that was used by one of the San Bernardino killers. The FBI wants to open the phone to determine the killer's contacts and messages. The phone is owned by the county government since the shooter was an employee. The FBI got permission from the county to inspect the phone and to retrieve data, especially back up records to the iCloud. But in order to do that, the FBI had to reset the iCloud password. By doing so, it de-coupled the back-up password key protocol to the actual phone. The FBI got the last synched back up data, but not what was on the phone leading up to the terrorist attack. Writs in common law are orders issued by a court in the name of a sovereign authority requiring the performance of a specific act. The most common modern writs are those, such as the summons, used to initiate an action to call a defendant to answer a complaint or to testify in court proceedings. Other writs may be used to enforce the judgment of a court ( attachment, delivery) or to require a lower court to furnish certain records (appeal or error) or telling an official perform a certain act (mandamus). Writs began to be used in judicial matters by the Norman kings, who developed set formulas for them. The most important were original writs, for beginning actions; in many instances they served much the same purpose as the modern summons. They were issued to the defendant, requiring that he make amends or else appear in court. Other important writs were those of assistance, for the transference of property, and entry, for the recovery of land from which one had been wrongfully dispossessed. In normal court proceedings, a party would issue a subpoena or warrant directed at a specific person or corporation to produce its business records or employees to testify on certain matters relevant to a specific case. There is no actual criminal proceeding against the two terrorists because they were killed in a gun battle. Apple had no direct involvement in the activities of the shooters. The FBI is trying to find out whether there were unknown accomplices. Some critics believe that the FBI is merely on a fishing expedition since it can gather that information from other sources. For example, the FBI can subpoena the telephone records for the cellphone user to determine who he spoke to on any given date. The FBI can then trace the phone logs to actual individuals. The FBI admits that it already has the back-up cloud data which should include contact lists and phone numbers used by the phone user. A normal subpoena for records to Apple would have gotten any iCloud back-up data. The government did obtain some data backed up to iCloud from the phone, but authorities allege in their court document that he may have disabled iCloud backups at some point. They obtained data backed up to iCloud a month before the shootings, but none closer to the date of the shooting when they say he is most likely to have used the phone to coordinate the attack. So, the FBI wants something that Apple does not possess: a key to unlock the phone security features. Apple's current iOS randomly creates a password encryption based on the owner's input code. Apple does not know what the encryption key is on any customer's phone. And since it is a random generator, Apple cannot re-create it. Apple created this security feature for the simple reason that more customers are using their phones for everything: calls, text, messages, banking and most importantly secured ApplePay at retail stores. Identity theft costs people more than $400 billion a year. The IRS hacks have cost individual taxpayers more than $6.9 billion in diverted income tax refunds. Anyone who has been the victim of ID theft can tell you it is a nightmare to try to correct your credit reports and banking transactions. There is a compelling interest to Apple to make the most secure iPhone. But the FBI dismisses Apple's reasons as mere marketing efforts for their product. It states that 14 people were murdered by the killers so it has a legitimate law enforcement interest in getting all the information off the killer's iPhone. But since the FBI cannot use a normal subpoena or warrant to get information from Apple (because it does not have an access key to the phone), the Justice Department is using a vague and archaic statute to try to compel Apple to assist the FBI. And the FBI states that with older iOS phones, Apple had cooperated and unlocked phones. But this is not about unlocking a phone; rather, it is about ordering Apple to create a new software tool to eliminate specific security protections the company built into its phone software to protect customer data. Opponents of the court's decision say this is no different than the controversial backdoor the FBI has been trying to force Apple and other companies to build into their software - - - except in this case, it is an after-market backdoor to be used selectively on phones the government is investigating. And that is the point of opponents: once the backdoor key is made, it will not be applied just to the San Bernardino case. And if get into the wild (or dark net), then Apple's security systems are brutally compromised with no recourse against the government.
The All Writs Act is a United States federal statute, codified at 28 USC Section 1651, which authorizes the United States federal courts to issue all writs necessary or appropriate in aid of their respective jurisdictions and agreeable to the usages and principles of law. The Act states: (a) The Supreme Court and all courts established by Act of Congress may issue all writs necessary or appropriate in aid of their respective jurisdictions and agreeable to the usages and principles of law. (b) An alternative writ or rule nisi may be issued by a justice or judge of a court which has jurisdiction. Application of the All Writs Act requires the fulfillment of four conditions: 1. The absence of alternative remedies: the act is only applicable when other judicial tools are not available. 2. An independent basis for jurisdiction: the act authorizes writs in aid of jurisdiction, but does not in itself create any federal subject-matter jurisdiction. 3. Necessary or appropriate in aid of jurisdiction: the writ must be necessary or appropriate to the particular case. 4. Usages and principles of law: the statute requires courts to issue writs “agreeable to the usages and principles of law.” In the case United States v. New York Telephone Co. 434 U.S. 159 (1977), the Supreme Court established a three-factor test for the admissible application of the All Writs Act: the party ordered to perform an action cannot be too far removed from the case, the government's request cannot impose an undue burden on that party, and the party's assistance is necessary. The case involved placing a pen register (recorder) on a telephone line of a suspect to gather information such as time, date, and telephone exchange numbers. The court believed that the telephone company was already collecting that data for billing and connection purposes so it would not be burdensome to comply with the writ. Apple will argue that the FBI cannot meet the burden established for the application of the Act. First, Apple is not a party to a criminal case. It is only involved because one of its products was owned by a suspected terrorist. Apple is a private party. It has no control over the device after it is purchased by a customer. Second, the FBI request is burdensome because what it asking Apple to do does not exist. The FBI wants Apple to program a new operating system program to disable the security features of the current iOS. It is estimated that it would take a team of 10 engineers at least a month to attempt to write such a codebreaker, plus months of beta testing to determine whether it works. Third, Apple's assistance is not needed by the FBI since it basically has all the back-up information from the cloud. Also, the government (though it will not admit it) buys zero day software hacks on the black market to spy on individuals and foreign governments. It retains its own cybersecurity experts including experienced coders. But what the FBI wants Apple to involuntarily force its employees to work for the government for free. Indentured servitudes were banned when slavery was abolished. Apple's lawyer, Ted Olson was blunt. “You can imagine every different law enforcement official telling Apple we want a new product to get into something,” Olson said. “Even a state judge could order Apple to build something. There's no stopping point. That would lead to a police state.” In a different 2015 case, Ken Dreifach, an Apple attorney argued: Even if the All Writs Act applies, it still cannot be used to accomplish the result that the government seeks. Apple does not possess or control the device. Rather, the government seeks to force Apple to take receipt of a device in the government's custody and provide what are essentially expert forensic services for the government by bypassing the security on that device to extract data belonging to the device's owner. This commandeering of Apple personnel and resources to do the government's investigative work is materially different from asking a communication service provider to access or provide data on its network or in its possession. What Apple is concerned about is a flood of writs compelling it to unlock iPhones or other devices. Currently, there are about a dozen pending cases asking Apple to perform some hack code to access information. In an ArsTechnia article, Rep. Ted Lieu (D-Calif.) said that allowing this order to stand would be a terrible decision. “This precedent-setting action will both weaken the privacy of Americans and hurt American businesses,” he said. “And how can the FBI ensure the software that it is forcing Apple to create won't fall into the wrong hands? Given the number of cyberbreaches in the federal government- - - including at the Department of Justice- - - the FBI cannot guarantee this backdoor software will not end up in the hands of hackers or other criminals.” Apple has spent millions of dollars on research and development to stop hackers and criminals from finding backdoors to corrupt its software and products. The FBI and federal officials want free access to Apple's highly guarded trade secrets and expertise. That is why many other technology companies and privacy groups back Apple's opposition to the FBI's requests. But proponents cite the judge's ruling in ordering the writ. The company is involved because it is their product. It is not burdensome because Apple's business is to create software code for its devices. And the FBI cannot get access to the phone contents without Apple's assistance. As WIRED explained, the shooter created a password to lock his phone, and due to security features built into the software on his device, the FBI cannot unlock the phone and access the data on it using the method it wants to use - - - a bruteforce password guessing technique wherein they enter different passcodes repeatedly until they guess the right one - - - without running the risk that the device will lock them out permanently. After six fails, Apple's software would permanently lock down the phone. Apple's operating system uses two factors to secure and decrypt data on the phone --- the password the user chooses and a unique 256-bit AES secret key thatŐs embedded in the phone when it is manufactured. The userŐs password gets “tangled” with the secret key to create a passcode key that both secures and unlocks data on the device. When the user enters the correct password, the phone performs a calculation that combines these two codes and if the result is the correct passcode, the device and data are unlocked. To prevent someone from brute-forcing the password, the device has a user-enabled function that limits the number of guesses someone can try before the passcode key gets erased. Although the data remains on the device, it cannot be decrypted and therefore becomes permanently inaccessible. Apple vows to fight theSan Bernardino case to the US Supreme Court. It has to fight because the government is asking it to weaken and destroy its most successful product, the iPhone. It makes little sense to weaken security for an entire industry for speculative government reasons to unlock one smart phone. At the end of February, a New York magistrate in a drug case ruled in Apple's favor. He ruled that the All Writs Act was not intended as the government argued when it is trying to force Apple to create a tool “against its will.” |
|
“The world stands aside to let anyone pass who knows where he is going.” - - - David Starr Jordan |
NEW EPISODE: |
 |
|
|
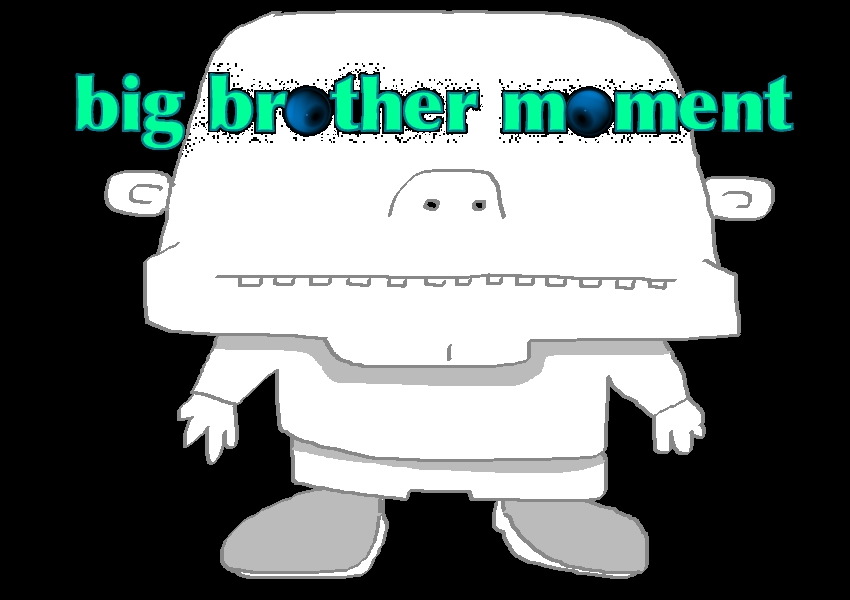
cyberbarf.com EXAMINE THE NET WAY OF LIFE cyberbarf ORWELLIAN FUTURE COMMENTARY Television viewers may be familiar with Big Brother, a UK reality series, which cameras are placed in a house filled with contestants to capture their crazy thoughts and actions. But the real Big Brother comes from George Orwell, whose real name was Eric Arthur Blair, English novelist born in India, who wrote two critically acclaimed novels Animal Farm (1945) and Nineteen Eighty-four (1949), the latter a profound anti-Utopian novel that examines the dangers of totalitarian rule. In 1944, Orwell finished Animal Farm, a political fable based on the story of the Russian Revolution and its betrayal by Joseph Stalin. In this book a group of barnyard animals overthrow and chase off their exploitative human masters and set up an egalitarian society of their own. Eventually the animals' intelligent and power-loving leaders, the pigs, subvert the revolution and form a dictatorship whose bondage is even more oppressive and heartless than that of their former human masters. The book foreshadows the rise of an elitist political class that exempts themselves from work, rules of law, and accountability for their actions. The book's most famous line is All animals are equal, but some animals are more equal than others. Orwell's last book, Nineteen Eighty-four (1949), is a novel he wrote as a warning after years of brooding on the twin menaces of Nazism and Stalinism that was affecting Europe. The novel is set in an imaginary future in which the world is dominated by three perpetually warring totalitarian police states. The book's hero, the Englishman Winston Smith, is a minor party functionary in one of these states. His longing for truth and decency leads him to secretly rebel against the government, which perpetuates its rule by systematically distorting the truth and continuously rewriting history to suit its own purposes. Smith has a love affair with a like-minded woman, but then they are both arrested by the Thought Police. The ensuing imprisonment, torture, and reeducation of Smith are intended not merely to break him physically or make him submit but to root out his independent mental existence and his spiritual dignity until he can love only the figure he previously most hated: the apparent leader of the party, Big Brother. Smith's surrender to the monstrous brainwashing techniques of his jailers is tragic enough, but the novel gains much of its power from the premises of totalitarianism to their logical end: the love of power and domination over others has acquired its perfected expression in the perpetual surveillance and omnipresent dishonesty of an unassailable and irresistible police state under whose rule every human virtue is slowly being suborned and extinguished. Orwell's warning of the potential dangers of totalitarianism made a deep impression on his contemporaries and upon subsequent readers, and the book's title and many of its coined words and phrases like Big Brother is watching you, newspeak, and doublethink became bywords for modern political or governmental abuses. Political correctness has been social engineering generations of Americans to accept a groupthink mentality. The anonymous nature of the internet has led people troll, blast and incinerate with impunity other people's views. The constitution affords freedom of speech, religion and association from government interference. The founding culture was that all views have merit but facts or the truth would rule the day. But not anymore. Personal opinion is now more important in public debates than actual factual basis for a view point. But what is really missing from public discourse is respect. If you do not absolutely accept my opinion, you are an idiot, a racist, a fool, a moron, or an elitist. Name cursing has taken the place of fact checks. People are hypersensitive to criticism. This thin-skin mentality may come from years of being protected by parents who bolster their kids self-esteem by telling them they are great and right even when they are wrong. Some people have lost the ability to stand up for themselves especially when they are being drowned out by a more vocal minority view. People are viewing the world through their own black and white prism not understanding that in a complex society there is more gray areas. Orwell's future is already here. There are security cameras on every street corner. There are red light traffic cameras automatically writing tickets (even when the timing is rigged against drivers clearing a yellow light). The national media is predominately pushing a liberal political agenda. The Internet is polarizing the political spectrum because any one can find some one else who shares their views, no matter how out-in-left-field those views are compared to the mainstream. People are fed up with their government. Congress' approval rating is around 10 percent. Citizens don't trust their elected officials. Government debt is crushing the middle class into bankruptcy. The next generations have started to abandon the ideal American Dream because the US economy has stagnated for decades. As a result, voter apathy has allowed career politicians to take hold of the reigns of power (the force of spending and taxation of the people). Politics has become so sleazy that decent, working class men or women cringe at the prospect of running for office because their opponents will rip them with lies, smears and assaults that it is not worth it. The two main parties are basically the same: labels attached to career politicians. It does not matter who is in power because spending continues to grow, debts skyrocket, and the blame game leads to no political accountability. Incumbents, who can't run an ice cream cart on a hot summer day, get re-elected 95 percent of the time. Unless you are indicted, in jail or have a sexual scandal involving minors, an elected official is almost guaranteed a job for life. America rebelled against the King of England because of the sovereign fiat over the colonists every day lives. Well, the United States has a de facto royal class of politicians and special interest lobbyists who control more than 20 percent of the gross domestic economy. But that is not enough. The Democrats still want a single payor (nationalized) health care system. Bernie Sanders wants everyone to have a free college education, paid by taxing the wealthy up to 92 percent of their income. But when the laws are written, the wealthy is defined as any middle class businessman who owns a factory, a sub shop or a professional firm. When 45 percent of working age Americans pay no federal income tax, the top one percent pay 700 times more income taxes than the average person. Since Congress continues to sell its votes on tax legislation through campaign donations, there are more exceptions for favored few than the average person. There comes a point when it is not worth it to be paying taxes for those who do not work or contribute to society. But the politicians promise the non-workers continued good benefits in exchange for their votes. It is all about controlling the public treasury. Unless there is an incentive to make individuals to make large profits, the system will collapse upon itself. And when this welfare class becomes upset that their benefits no longer meet the realities of grocery inflation, the politicians are willing to import millions of new immigrants to become stealth voters. No one doubts that state and federal corruption is running rampant. Welfare, Medicaid, Medicare fraud is costing the system hundreds of billions of dollars. Crony capitalism is where the government determines which businesses will be winners and which will be losers. The bailout of the major banks is a prime example of special intervention policies with massive spending to prop up incompetent to alleged illegal behavior. And that is another mark of a failing culture. Bad behavior is being rewarded more than hard work. Reality TV stars make millions for doing nothing except acting stupid on the television. Donald Trump has connected with this viewership. America loves the cult of personality. Trump has taken his Apprentice reality show and turned into a presidential campaign. And despite his bellowing, boasting, screaming, insults and total lack of command of the issues, he has galvanized the disenchanted independent voters to support him. Going into Super Tuesday primaries, Trump is gathering one third more votes than the last GOP nominee, Milt Romney. Analysts believe that the only way to stop a Trump nomination is if he loses Ohio and Florida. If not, then the GOP establishment will have to back him in the campaign imperative: anybody but Hillary. But no one knows what Trump stands for. He was once a registered Democrat. He contributed to Bill Clinton's campaigns. He says that being a New Yorker and a businessman, he gives money to politicians to keep access and communications with the powerful. He has a point; Wall Street gives more money to Democratic candidates than Republicans even though Dem candidates curse against Wall Street. That is the game: bait and switch the voters. This 2016 campaign has a 1930s Germany vibe. Hitler did not seize power, he was elected by a disenfranchised populist majority. He railed against an enemy of the state, the Jewish merchant class, as being the source of the nation's ills. Once in office, he became a maniac dictator obsessed with power which led to World War II. There are parallels to a highly educated country electing a mad man to power. Trump throws out crazy ideas at his stump speeches, including stopping all Muslims from coming the United States in order to stop terrorism. Trump also wants to gut the First Amendment to make libel laws more plaintiff friendly. Why? Because he can get around a public figure defense to sue his critics into submission. That is the Trump business model: if he can't get his way he threatens to or sues his opponents with a scorched earth litigation free-for-all. Since he has the resources, he can brow beat down his court opponents through long and costly litigation. (Ironically, Trump may have to testify as a named defendant in a fraud case right around the time of the GOP convention.) On the other end of the line, Facebook's Mark Zuckerberg is calling for his business to censor any hate speech against Muslims. He does not realize that if you create a town square and invite the public into it, there will be various levels of animosity and offensive speech. What he does not realize that free speech includes offensive speech. When the Nazi Party marched through a predominately Jewish suburb of Chicago, the courts ruled that the city could not deny the Nazi's a permit to march. Even though the vast majority of people in the city and country are against the message of these skinheads, the First Amendment protects their right to march, protest or speak. In the end, the majority ignored them and this group slowly faded from the scene. It is the confrontation that fuels people to continue to act out their emotions. The Internet has created a new addictive substance: digital popularity. The number of likes, friends, comments or Twitter wars makes some people feel more alive. Politicians try to tap into this popularity mentality to herd voters to their cause. That is why politicians promise anything to any group, even it is inconsistent with their own voting records, because many followers are single issue voters. By the time a candidate is in office, it is too late. Many Obama supporters confess that they were caught up on the Hope and Change message of the Obama campaign. They wanted to be part of history; electing the first Black president. But no Hope and Change happened to his electorate. In fact, his adopted hometown, Chicago, has slid into a wild west daily shooting gallery of gangs versus police and police verus the community. Most thought that Obama would protect individual rights like the First and Fourth Amendments. But his Justice and Intelligence Departments has become so anal on security and surveillance. that they have continually misled Congress on meta-data collection techniques. Civil libertarians cringe at the amount of personal liberties being trampled by government spying on its own citizens under the guise of national security. The erosion of personal freedoms leads to more intrusive government regulation beyond mere claims of security. For example, local zoning has grown so pre-emptive that many city councils will tell property owners what color brick they have to use on their new home. It really is none of the government's business on what color a person's house is. But under the guise of health, safety and welfare, cities try to impose their collective sensibilities and aesthetics on their community because they can get away with it. The Supreme Court has allowed expanded eminent domain laws to take private property by a municipality who then immediately turns it over to a private developer under the guise of economic development. There is nothing in the constitution that grants “economic development” to government agencies. All unspoken rights were reserved to the people. Protection of property rights was a centerpiece of opportunity and the American Dream. So now every strip mall in Suburbia looks exactly the same. Every subdivision has a cookie-cutter sense of blandness. Personal expression and choice is being replaced by government will. The 2016 campaign should be discussing and deciding these important personal freedoms. But in the click bait, soundbite media culture, the Republican debate turns into temper tantrums between three-year-olds while the Democrats yell more and more unsustainable promises in order to buy votes. It would make as much sense to crown the 2016th driver through the Pennsylvania Turnpike toll booth on November 4th the next President. In the counter attacks of character and alleged lack of qualifications to run the country, we find ourselves in the future history pages listening to rabid dogs rather than statesmen. None of the presidential candidates give the aura of any confidence that they will actually protect the Bill of Rights from their own prospective administrations. In fact, secrecy and power brokering insider politics seems to be the standard operating procedure for Hillary Clinton. The email scandal of top secret data being found on her personal, insecure home computer system has been discounted by the candidate then the media even though several government workers have been indicted (and jailed) for less breaches of security. This is just another example of how corruption is so common place that public officials believe that they are above the law because they write or enforce it. It is this elitist political culture that is sucking the freedoms of individuals into the caldron of power-addicted idiots. It is clear that modern politicians like Trump and Hillary have gone from being arrogant toward the average citizen, to contempt and now disdain. With the government and courts eroding individual freedoms, and the presidential candidates not talking about the values of American liberties, the nation will continue to balance itself on a tightrope over the deep, dark canyon of Big Brother.
cyberbarf iToons
|
 |
|
cyberbarf THE WHETHER REPORT |
cyberbarf STATUS |
| Question: Whether if the FBI's writ to Apple to create a backdoor tool to decrypt an iPhone is upheld, it will lead to major security issues in the future? |
* Educated Guess * Possible * Probable * Beyond a Reasonable Doubt * Doubtful * Vapor Dream |
| Question: Whether the anti-establishment voter backlash will propel an anti-freedom candidate to the presidency? |
* Educated Guess * Possible * Probable * Beyond a Reasonable Doubt * Doubtful * Vapor Dream |
| Question: Whether the American political system is broken by corruption, special interests and apathetic public? |
* Educated Guess * Possible * Probable * Beyond a Reasonable Doubt * Doubtful * Vapor Dream |
|
LADIES' JAMS MULTIPLE STYLES-COLORS $31.99 PRICES TO SUBJECT TO CHANGE PLEASE REVIEW E-STORE SITE FOR CURRENT SALES
|
PRICES SUBJECT TO CHANGE; PLEASE CHECK STORE THANK YOU FOR YOUR SUPPORT!
NEW REAL NEWS KOMIX! SHOW HACK! |
|
PRICES TO SUBJECT TO CHANGE PLEASE REVIEW E-STORE SITE FOR CURRENT SALES & CURRENT STYLES
|
|
THE PINDERMEDIA STORE IS FULL OF FUN T-SHIRTS CLOTHES, HATS AND OTHER ITEMS. CHECK OUT THE STORE FOR ITEMS
SUPPORT cyberbarf VISIT THE CYBERBARF STORE! Prices and styles may vary depending on sales, allotments, inventory. |
|
BACK IN BLACK WITH THIS CLASSIC CYBERBARF T-SHIRT!
FEATURING: THE REAL NEWS IMPACT EDITORIAL CARTOONS WRIGLEYVILLE WAR POLITICS ENDORPHIN RUSH THE DARK ABYSS RANDOM ELECTRONS SPECIALS
PORTFOLIOS OF SKI EDITORIAL CARTOONS ILLUSTRATIONS PHOTOGRAPHY |
NEW THEORIES AND CHARACTER ESSAYS INCLUDING 10 YEAR ANNIVERSARY ARTICLES
cyberbarf
THE STEAM PUNK SPECIAL EDITION featured new Music from Chicago Ski & the (audio) Real News: (mp3/4:14 length)
EXAMINING THE NET WAY OF LIFE cyberbarf™ distributed by pindermedia.com, inc.
|
cyberbarf
Distribution ©2001-2016 pindermedia.com, inc.
All Ski graphics, designs, cartoons and images copyrighted.
All Rights Reserved Worldwide.