|
JULY 2013 IN THIS ISSUE:
LIT FOR TWIT BARFERATURE BLACK & WHITE & SEEING RED ALL OVER BENDS & TRENDS iTOONS SNAPSHOT IN JOURNALISM WHETHER REPORT NEW REAL NEWS KOMIX! SHOW HACK!
|
|
cyberbarf EXAMINE THE NET WAY OF LIFE
For every ending, there is a new beginning: NEW REAL NEWS KOMIX! SHOW HACK!
CYBERBARF T-SHIRTS, MUGS & MORE
THANK YOU FOR YOUR SUPPORT!
CYBERBARF
THANK YOUR FOR YOUR CONTINUED SUPPORT.
|
|
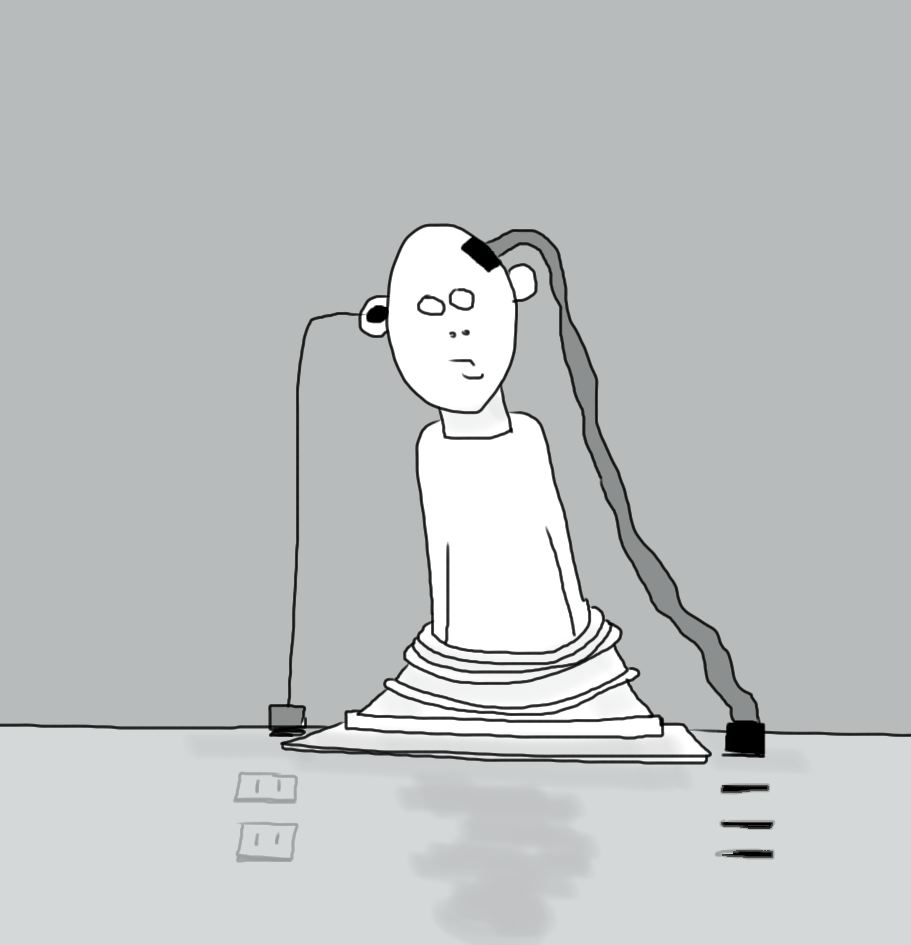
cyberbarf LIT FOR TWIT BARFERATURE As we have mentioned before, the whole 140 character messaging limitation of Twitter has fostered the ill of people unable or unwilling to make comprehensive sentences for their text messages. Other critics have thought the issue of the character restriction has spawned a generation of grammerless acron-text smiths who have lost the art of word imagery. But it also made some scholars think they could tame the Twitter message beast by concentrating a story into 140 characters or less. Well, that is a challenge which we decided to take to this page. Instead of merely stringing words together, we decided to blend graphics to the twitterature structure to create the mosaic form of new expression we call BARFERATURE. Our seventh BARFERATURE story board is called: HELLO.
cyberbarf EXAMINE THE NET WAY OF LIFE
cyberbarf BLACK & WHITE & SEEING RED ALL OVER CYBERRIGHTS Civil libertarians from both sides of the political spectrum are up in arms over the National Security Agency's overbroad attempts to seize every American's telephone and email records. The vast amount of secret data being collected under the guise of security has the average American pausing to reflect on what privacy, if any, they have left. The sobering fact is that we have very little left; what has been taken away may be lost forever. In the last seven years, the NSA is aware of every telephone call you have made. It knows whom you called, how long you talked and the location of the participants. That type of information is collected in the “metadata” collected from telephone company call records. The government's collection of this data was under the guise of fighting terrorism since the 9/11 attacks. It may have started in the Bush Administration, but it was clearly ramped up in the Obama Administration. The vast amount of personal data being collected by government agencies is extremely troubling to civil libertarians. George Washington University law professor Orin Kerr noted that if NSA personnel “have an order for phone calls, they could also have it for emails and other electronic records.” The Washington Post reported, “The National Security Agency and the FBI are tapping directly into the central servers of nine leading U.S. Internet companies, extracting audio, video, photographs, emails, documents and connection logs that enable analysts to track a person's movements and contacts over time.” The general consensus had been that the U.S. government and agencies such as the CIA had no right to run domestic surveillance programs against United States citizens. All spying and intelligence gathering was directed toward foreigners and other nations. This was true because the Constitution limited government's intrusion into the personal lives of the American people. The Constitution bans unreasonable searches and seizures, so the government normally can get a warrant to invade someone's home and papers only if it has tangible grounds to think the person did something illegal and only if it specifies what it's looking for. Searches require what lawyers refer to as individualized suspicion. In this year's Supreme Court decision allowing police to take DNA swabs from felony arrestees, Justice Antonin Scalia noted in his dissent the importance of constitutional history in our modern times. “At the time of the Founding, Americans despised the British use of so-called 'general warrants' -- warrants not grounded upon a sworn oath of a specific infraction by a particular individual, and thus not limited in scope and application.” The British had used these general orders to harass, punish, steal and terrorize the colonists. The Fourth Amendment was intended to prevent such warrants. The dissenting conservative Justice was aware of the noble purpose of facilitating public protection. “Solving unsolved crimes is a noble objective, but it occupies a lower place in the American pantheon of noble objectives than the protection of our people from suspicionless law-enforcement searches.” It is classic case that even the most noble purpose does not justify unconstitutional means. Even experts who normally side with the government in anti-terrorism measures were taken aback by this voluminous dragnet. Brookings Institution scholar Benjamin Wittes noted that the law is supposed to allow the government to get only “foreign intelligence information” that is “relevant to an authorized investigation.” The collection of all the data to find one small needle in a haystack the size of the United States is excessive. In fact, during Congressional testimony, the proponents of the data collection plans only could state that 50 terrorists plots were foiled by the use of the data capture and “ chatter” disclosed between terror cell members. (Some local police agencies dispute that it was even 50 such events). But it the NSA is collecting more than one billion telecom records per day, the success rate equal 50/(1,000,000,000 x 365) x 12 or a power microscope needed to find the decimal point result. Big data system managers agree that trying to handle vast amounts of data to look for specific patterns is an impossible challenge. In order to extract any meaningful information, one needs to set up valid parameter points and filter algorithms to match the variables or plot points to get useful results. For example, an ISP or search engine company like Google will cache your cookies (ISP address and information) and then collect your click data to other ISP addresses or web page content (keywords) to then “push” or send feedback to your screen, in the terms of a direct, personalized advertisement. This is a simple matching game compared to the NSA's delusion of trying to automatically filter out security threats of billions of communications in real time. The security wonks believe in the basketball playground rule, “no harm, no foul.” Innocent people have nothing to hide, so they should not mind if the government comes across their “innocent” data in search of crimes. The problem with indiscriminate ransacking of homes and effects is not that it's ineffective in finding wrongdoing. It's that the innocent people should not be punished in the pursuit of the guilty. It's that the need to protect the safety of the public has to be balanced against preserving the privacy of the individual. President Obama thinks you really shouldn't worry about all this. Obama said before he was president he, too, had “a healthy skepticism” of the aggressive intelligence services, but now, with further safeguards, which he did not identify, he decided that snooping is worth it. “You can’t have 100 percent security, and also then have 100 percent privacy and zero inconvenience,” he stated. A presidential spokesman added that the phone surveillance program “has been a critical tool in protecting the nation from terrorist threats.” The power of the presidency does tempt the forces of corruption, as seen in the other scandals plaguing the administration, including the IRS actions against the President's political opponents. There is a dark pattern emerging from how the government collects personal data and how it can use it against political opponents or causes. Civil libertarians ask two simple questions: Why should we believe what the government says? And what have we as a people lost? Trust us. Would your government — and the private contractors your government hires to do the work — do anything bad? According to the cries of those same bureaucrats and contractors, the answer is YES since it was one of their own, a computer tech named Edward Snowden, who accessed the secret data, copied it and published it to the world in alleged violation of several U.S. laws and the government's own security protocols. The statement that one cannot have 100 percent security and also then have 100 percent privacy and zero inconvenience is an illogical construction of different propositions. Security is taking objective, public measures to make it more difficult to criminals to act, such as putting locks on gates, cameras at ATM stations, or armed guards in bank lobbies. None of those security measures has any bearing on a business or a bank reducing a customer's financial privacy or personal information. It is part of a growing dilution of core concepts by officials who look to make their jobs easier in a power vacuum. These pundits believe there is a difference between constitutional searches and “regulatory” searches. Since the airline industry is heavily regulated, the government forced passenger searches and boarding pass restrictions after 9/11. Those searches became more and more intrusive to the point of full body x-ray objections by the general public. The regulators walked their authority to the public breaking point and kept the power to search passengers without a warrant or suspicion. Even though those citizens have numerous constitutional rights including the right to freely travel and to not be indiscriminately searched by government officials. But the general public blindly agreed to these searches under the purpose of public safety. The Administration and its officials tried to calm the Congressional questions on the NSA scandals. James Clapper, director of US intelligence , acknowledged that these programs “cannot be used to intentionally target any US citizen, any other US persons located outside the United States.” That would be against current law. But he used the word “intentionally,” which does not rule out unintended sweeps of anyone personal data. He would later admit that he used the wording in his answer to give the less untruthful answer possible under the circumstances. In all respects, his answer made no sense in the scale of the data collection programs themselves. The Washington Post reported that while in one surveillance program American citizens are not “intended” to be targets of surveillance, large quantities of “content” from Americans are nevertheless screened to track or learn more about a target. At another hearing, Clapper was asked point blank where the government had the capacity to listen in on telephone calls or read people's emails. His answer was “No, we do not have the authority to do that.” Again, it was another misleading answer to a direct question. That is parroting existing law, but not answering the question whether the NSA has the means to break the law. The NSA does not have the authority to collect private citizen information, but it did so anyway by forcing telephone and internet companies to supply the data under secret court orders. Fear is great motivation. After 9/11, the politicians used fear of further attacks to persuade us to give them more power to stop future acts of terror. We tolerated the intrusions of the security state, the groping in the long lines at the airports, the barriers around government buildings. George W. Bush even allowed the Secret Service to close Pennsylvania Avenue in front of the White House. In a fit of fear we assumed, as Peggy Noonan observed in the Wall Street Journal, that “we’ll just do it now, and down the road we can stop it. It’s just an emergency thing. We can make it go away when we no longer want it. But can we? Do government programs tend to remain static, or wither? Or do they tend to grow?” Intelligence services are beasts that grow with power. They look for short-cuts and quicker ways to get information to digest. The NSA once urged President Bush to “rethink” the Fourth Amendment in the wake of the 9/11 attacks. NSA officials argued that the Fourth Amendment was an archaic element from the past with little relevance today since in the Information Age causes government to rethink and reapply the procedures, policies and authorities born in an earlier electronic surveillance environment. It is the overall thought process of these officials that should concern citizens as much or more than the domestic spying programs. It is clear that the Obama administration has conceit for gun rights afforded under the Second Amendment. The Obama administration is unwilling to recognize the role or scope of the First Amendment, with its Justice Department labeling a reporter doing his job as a criminal co-conspirator in a leak investigation. It now has tossed aside the Fourth Amendment to seize personal information without a valid warrant. President Obama insists that nobody at the NSA is listening to anybody’s telephone calls. That may be true. But since the administration is more concerned about getting around Constitutional roadblocks, and its officials testimony on the subject has been misleading lies, no one cannot be sure. They may not have to listen at all. The aggregated metadata collected and analyzed by computer technology may be more revealing than its content. Two NSA whistleblowers, J. Kirk Wiebe and Billy Binney, told Fox News when the government’s computers collect information “about you that includes locations, bank transactions, credit card transactions, travel plans, EZ Pass on and off tollways; all of that can be time-lined. To track you day to day to the point where people can get insight into your intentions and what you’re going to do next.” The “innocent” metadata can see who you call and for how long, see what bills you pay and when, your favorite restaurants and what you usually eat, even how many glasses of wine you order to go with your dinner. This electronic trail is as valuable as a private investigator following a person around town 24/7. This type of personal tracking information would be extremely valuable to divorce attorneys, blackmailers, collection agencies, stalkers, political consultants, political campaigns and private marketing firms who pay big money for data mined consumer files. In the IRS scandal, it is alleged that IRS workers singled out conservative groups seeking tax exempt status to raise funds to run issue oriented campaigns. The intrusive questions about confidential donor information and stone walling approval process could have affected the last election. Many tea party donors found their personal returns suddenly audited or their place of businesses raided by other agencies, such as OSHA. It was also alleged that IRS officials leaked personal donor information to the press to smear or suppress donor activities that conflicted with administration policies or goals. There is no reason to believe that the NSA files could not be used in a similar fashion to abuse, harass or extort political opponents.
At some base level, government officials must view Good Citizens as pawns or zoo animals. Citizens are only needed to be milked of their tax dollars, their votes, and now their personal information. Good Citizens are taught from an early age to trust their government officials, that the police are not the enemy, and politicians are your concerned friends. They are conditioned to believe that no government agency would ever lie, cheat and steal from them. Because the vast amount of personal information breach scandals and the scope of those data sweeps, the trust factor between citizens and their officials has been breached. When NSA officials told Congress that the amount of information stored can only be accessed with a search warrant, skeptics sighed in disbelief. The NSA officials stated that once a suspect is identified, it would get his or her telephone number and then obtain a search warrant to access the data base records that it already had seized months or years earlier. The NSA is like the worst digital file hoarder; the creepy electronic peeping-tom. But nothing, including lax oversight, would stop anyone with NSA clearance from accessing the stored information at any time, without a warrant. Besides, if the NSA or FBI has a suspect and wants that digital information of phone records and contacts, it can obtain a normal court warrant to obtain the telephone company those same (but individualized) records directly, without snatching up a hundred million other customer records in the process. Unlikely alliances are being formed as a result of these scandals. The ACLU, libertarians, the Electronic Freedom Foundation, and representative of both major political parties have joined in the outrage over the spying programs. Even the companies involved like Verizon, Google and Apple have asked the government to allow them to explain to their customers and shareholders their involvement in these cases, to fend off the massive negative public relations hit. Those companies are under a blanket gag order to not reveal anything about the FISA court turnover orders, including the orders themselves. Yahoo has released a statement that it had to comply after fighting the proposed order on constitutional and privacy grounds. Over time, the companies which are on the cutting edge of building network infrastructure and data management, become consultants to the NSA, CIA and FBI who piggyback on their inventive work to use it as spy tools. The government needs the private sector to help it corral the massive amount of data it wants to collect on a daily basis. NSA operates many network “tap” operations both in the US and around the world. NSA faced a few major problems with that vast stream of data. Storing it, indexing it, and analyzing it in volume required technology beyond what was generally available commercially. Considering that, according to Cisco, the total world Internet traffic for 2012 was 1.1 exabytes per day is physically impossible, let alone practical, for the NSA to capture and retain even a fraction of the world's Internet traffic on a daily basis. There's also the issue of intercepting packets protected by Secure Socket Layer (SSL) encryption. Breaking encryption of SSL-protected traffic is, under the best of circumstances, computationally costly and can't be applied across the whole of Internet traffic (despite the apparent certificate-cracking success demonstrated by the Flame malware attack on Iran). So while the NSA can probably do it, they probably can't do it in real-time. That is why the agency seeks court turnover orders and massive data storage facilities so it can come back to review the data at a later time. It is also why government outsourcing is a huge business. Private companies are retained at top dollar to help the government in its activities, including gathering intelligence. The U.K. Guardian newspaper reported the NSA is still collecting call data records for all domestic calls and calls between U.S . and foreign numbers—except now the agency is armed with FISA warrants. The broad FISA orders grant “comprehensive communications routing information, including but not limited to session identifying information (e.g., originating and terminating telephone number, International Mobile Subscriber Identity (IMEI) number, etc.), trunk identifier, telephone calling card numbers, and time and duration of call. ” In 2006, USA Today called the call database “the largest database in the world. ” That transactional record data for billions upon billions of phone calls presents a physical-space problem on a similar scale to that which the NSA encountered in its Internet monitoring (the PRISM program). Ars Technica reported that Internet companies such as Google and Yahoo were solving their own big data storage and analysis problem. In November of 2006, Google created BigTable, a database with petabytes of capacity capable of indexing the Web and supporting Google Earth and other of its applications. Yahoo had a similar operation called the Hadoop. BigTable and Hadoop-based databases offered a way to handle huge amounts of data like being captured by the NSA's operations, but the private systems lacked something critical to intelligence operations: compartmentalized security (or any security at all, for that matter). So in 2008, NSA set out to create a better secured version of BigTable, called Accumulo—with the capability that allows individual items within a row of data to have different classifications. That allows users and applications with different levels of authorization to access data but see more or less information based on what each column's “visibility” is. Users with lower levels of clearance wouldn't be aware that the column of data they're prohibited from viewing existed. Accumulo also can generate near real-time reports from specific patterns in data. So, for instance, the system could look for specific words or addressees in e-mail messages that come from a range of IP addresses; or, it could look for phone numbers that are two degrees of separation from a target's phone number. Then it can spit those chosen e-mails or phone numbers into another database, where NSA workers could peruse it at their leisure. In other words, Accumulo allows the NSA to do what Google does with your e-mails and Web searches—only with everything that flows across the Internet, or with every phone call you make. It is that amount of access to personal information that has people alarmed; this is Big Brother coming to life.
However, there are defenders of the surveillance programs. Some people believe that the cost of stopping another 9/11 terror attack is worth allowing the NSA to collect and store personal information like a bank or telephone company does with its customer data. However, other people merely set off the attack the messengers who object to the programs. Salon.com railed against libertarians in the wake of the NSA spying scandal. The author asked the question “If libertarianism is such a good idea, why aren’t there any libertarian countries?" While most people struggle to find the answer, it is sitting right before their eyes. A major country was founded upon the principles of individual rights, personal freedom and liberties, and small limited government whose authority came not from a king or elite ruling class but from the people. That country was the United States of America. Reason Magazine's counterpunched on the phony argument raised by such Democratic mouthpieces. There are many idealistic progressives who've remained opposed to the National Security Agency's data mining programs regardless of who is in the White House. They agree with the principle that we can't surrender our freedom for safety. However, these same people have such little reverence for constitutional liberties in other areas of public life. Liberals place a moral imperative on all Americans to scale back personal liberty to allegedly build a cleaner, fairer and healthier world (in a Nanny State way). Soon after news of the NSA's data mining and PRISM programs hit the news, many Democrats attacked Snowden, the Guardian, the Washington Post, reporters and commentators who dared challenge the authority and intentions of the President or his administration. Even in the midst of evidence that the administration was part of a new intrusive police state. In January 2006, when George W. Bush was president, Pew Research Center asked Democrats how they felt about the NSA's surveillance programs. Thirty-seven percent labeled the spying “acceptable,” and 61 percent said they were unacceptable. The reverse is true today, as 64 percent of Democrats believe that Barack Obama's surveillance programs are acceptable and 34 percent say they're not. Partisan politics of Washington and cable “news” creates mass hypocrisy depending on which political party is charge of the snooping. But it's those Democrats who now use the concept of “safety” as the basis for increasing government power, when at the same time they continue to add roadblocks for “personal safety” rights of law abiding Americans such as expand government-run background checks on firearms or giving the Internal Revenue Service unlimited access to your personal financial and health care records as part of Obamacare. Government should be transparent so the people can check out their representatives and correct fraud and abuse. But it is government and elected officials who are pushing a faux transparency principle on the people to coerces every American citizen to report the status of his health insurance to the IRS or allow the NSA to copy all of their digital foot prints. Some commentators believe that the concern about these NSA programs is likely driven by an antipathy toward the war on terror rather than a concern about the corroding of constitutional protections. There is always a crisis that politicians claim only they can solve. There is always a mysterious villain in today's political discourse which needs to be tempered or put away. And the only way to do so is for the people to grant their officials, directly or indirectly, more power. H.L. Mencken said “The whole aim of practical politics is to keep the populace alarmed (and hence clamorous to be led to safety) by menacing it with an endless series of hobgoblins, all of them imaginary.” There is real truth that any large government program is subject to corruption. Power corrupts and absolute power corrupts absolutely. In the U.S., there are numerous federal and state financial and health care privacy laws which protect an individual's information, health history, and business transactions from third party publication. Thousands of technology, finance and manufacturing companies are working closely with US national security agencies, providing sensitive information and in return receiving In addition to private communications, information about equipment specifications and data needed for the Internet to work -- much of which isn’t subject to oversight because it doesn’t involve private communications -- is valuable to intelligence, U.S. law-enforcement officials and the military. The government passes numerous privacy laws but then it refuses to enforce or obey them when it comes to government business. Bloomberg News reported thousands of companies, from finance to manufacturing and technology, have been providing sensitive information to the United States government in exchange for benefits that include access to classified intelligence. According to the report, these programs, whose participants are known as “trusted partners,” extend far beyond what was revealed by whistleblower Snowden, a computer technician who did work for the National Security Agency. The role of private companies has come under intense scrutiny since his disclosure this month that the NSA is collecting millions of U.S. residents’ telephone records and the computer communications of foreigners from Google and other Internet companies under court order. Many of these same Internet and telecommunications companies voluntarily provide U.S. intelligence organizations with additional data, such as equipment specifications, that don’t involve private communications of their customers. But it does give government agencies the keys to open their systems to record seizures. Makers of hardware and software, banks, Internet security providers, satellite telecommunications companies and many other companies also participate in the government programs. In some cases, the information gathered may be used not just to defend the nation but to help infiltrate computers of its adversaries. Along with the NSA, the Central Intelligence Agency the Federal Bureau of Investigation and branches of the U.S. military have agreements with such companies to gather data that might seem innocuous but could be highly useful in the hands of U.S. intelligence or cyber warfare units, Bloomberg sources stated. The trusted partnerships can lead to crony capitalism and corporate espionage as the government can pit private companies against each other to curry favor (and information). Bloomberg News also reported that a former general counsel for the NSA, said if metadata involved communications between two foreign computers that just happened to be crossing a U.S. fiber optic cable “then the likelihood is it would demand less legal scrutiny than when communications are being extracted one by one.” Any hint of a foreign connection in intercepting messages is the excuse to avoid following any Constitutional warrant procedures. In addition, lawmakers who are supposed to oversee U.S. intelligence agencies may not understand the significance of some of the metadata being collected, said Jacob Olcott, a former cybersecurity assistant for Senator John D. Rockefeller IV of West Virginia, the Democratic chairman of the Senate Commerce Committee. “That’s what makes this issue of oversight so challenging,” said Olcott . “You have a situation where the technology and technical policy is far outpacing the background and expertise of most elected members of Congress or their staffs.” So Congressional oversight may be as rubber stamp as the secret FISA court judges. While companies are offered powerful inducements to cooperate with U.S. intelligence, many executives are motivated by patriotism or a sense they are defending national security, the people familiar with the trusted partner programs told Bloomberg news. U.S. global telecommunications, Internet, power companies and others provide U.S. intelligence agencies with details of their systems’ architecture or equipment schematics so the agencies can analyze potential vulnerabilities. “It's natural behavior for governments to want to know about the country’s critical infrastructure,” said a corporate security officer. Even strictly defensive systems can have unintended consequences for privacy. Einstein 3, a costly program originally developed by the NSA, is meant to protect government systems from hackers. The program, which has been made public and is being installed, will closely analyze the billions of e-mails sent to government computers every year to see if they contain spy tools or malicious software. Einstein 3 could also expose the private content of the e-mails under certain circumstances, according to a person familiar with the system. Therefore, agencies such as NSA are spying on themselves. There is a paranoia throughout these scandals which points again to the main theme of Big Brother. So, with all these sophisticated programs and advanced technology, how secure is the United States and its agencies? Objectively, not so secure. It was fairly obvious to most foreign nations that the Americans were spying on their communications. The U.S. was always reacting to foreign cyberattacks. It was monitoring cell phone communications to track terrorist leaders in the Middle East, including hacking emails and web pages. No one should be surprised by the revelation that the U.S. maintained a sophisticated electronic spy network. What was surprising was the story that the U.S. was spying on its own people. In such a blanket warrantless data collection, U.S. officials basically turned the Constitution inside-out: you were assumed guilty until you proved your innocence. This set off the intense policy debate across the country. Whistleblower Snowden first came off as a sympathetic hero. He disclosed that his government was gathering vasts amount of personal data on U.S. citizens without clear constitutional safeguards. If he just kept to the policy specifics and amount of information the government has access to he would not have been in legal trouble. But it was learned that he may have copied confidential and secret government documents and program keys. No matter what noble purpose, taking classified government documents is a crime. Further, when Snowden continued to talk about his role in this matter, it started to become clear that he may have been a mole from the beginning bolstered by outside enablers such as the Wikileaks organization, whose mission is to embarrass the U.S. government. Snowden is now in hiding after being indicted in the United States. But even as these scandals begin to cool, it is doubtful that anything will really change. The spies will continue to spy. The government will continue to whittle away at personal liberties. The people will go on with their apathetic lives until some government intrusion affects them on a direct personal level. The big data bank players will continue to cull personal information and sell it to marketing firms. People's privacy will narrow to that of a peep show.
cyberbarf BENDS & TRENDS
It's back after nearly a decade, Bends & Trends, quick hits on what is good and bad in cyberculture.
|
|
THE PINDERMEDIA STORE IS FULL OF FUN T-SHIRTS CLOTHES, HATS AND OTHER ITEMS. CHECK OUT THE STORE FOR ITEMS
SUPPORT cyberbarf VISIT THE CYBERBARF STORE! Prices may vary depending on sales, allotments, inventory. |
|
cyberbarf.com EXAMINE THE NET WAY OF LIFE iToons
cyberbarf SNAPSHOT IN JOURNALISM ESSAY The Chicago Sun Times laid off its entire photography department. It was a shocking turn in events. How can a newspaper in the third largest city in the US function without a photo staff? Editors told the remaining reporters to go to iPhone photo training sessions. Editors would also use freelance photographers, on a need only basis, paying anywhere from $60 to $135 per assignment, with condescending conditions on the number, type and quality of submissions. Nothing was more apparent in this gaffe than in the Blackhawks championship celebration. If there was ever a “photo” event of a parade and Grant Park rally, this was it. The Chicago Tribune had numerous photographers in the heart of the parade route and near the stage to collect the rabid joy on Hawks players and fans. The Sun Times started its coverage with a long shot across the park, then followed up with distant iPhone quality pictures of the crowds. Some of the S-T photos were unaccredited or made by its own reporters. It used only one AP photo of the ceremony near the stage. Newspaper photographers are photojournalists. They tell the story in pictures and in the caption. A good picture is worth a thousand words. So why would a newspaper cut half its journalism staff? To save salary, benefits and employment taxes. The Sun Times is in financial trouble. There is a billing dispute with the Tribune over unpaid invoices for Tribune's printing ST editions. Newspaper advertising revenues continue to dwindle. Paid circulation is also faltering. The whole industry is in a fiscal downward spiral. Layoffs and job consolidations are now more common place. Reporters and editors are now being forced to do two or three displaced persons jobs. A reporter is now a reporter, a photographer, and their own primary story copy editor. Three jobs in one paycheck may work for an accountant, but it does not serve the news room or readers well. There is no question that the quality of the photographs published by the ST will diminish. Reporters using their smart phones to capture pictures of events is not the same as a trained professional. Freelancers may have more technical skills, but since they are not newspaper employees there is little loyalty or availability to cover breaking events which an editor has with a staff photographer. It is ironic that the diminished newspaper product created by large staff cuts is also contributing to the large declines in readership. Readers are not stupid. They can see when a local paper is not covering local events. They can see the quality of work decreasing as the news holes shrink and the papers themselves look like car wash advertising flyers. Readers will take the cue that the publisher has given up on created a quality product and the readers will stop buying or reading that publication. And the alleged saving grace of moving content to a digital portal has been an industry disaster. The digital editions never captured the lost revenue streams of a robust newspaper's classified advertising and bulky ad inserts. When the Sun Times laid off its entire photography staff, it took a snap shot of itself. It's own obituary.
|
|
cyberbarf THE WHETHER REPORT |
cyberbarf STATUS |
| Question: Whether personal encryption devices will be the next Wave in must-have technology? |
* Educated Guess * Possible * Probable * Beyond a Reasonable Doubt * Doubtful * Vapor Dream |
| Question: Whether security issues will plague cloud service providers in the near future? |
* Educated Guess * Possible * Probable * Beyond a Reasonable Doubt * Doubtful * Vapor Dream |
| Question: Whether more and more states will pass laws to obstruct or nullify enforcement of federal mandates? |
* Educated Guess * Possible * Probable * Beyond a Reasonable Doubt * Doubtful * Vapor Dream |
|
cyberbarf EXAMINE THE NET WAY OF LIFE |
Bureaucracy defends the status quo long past the time when the quo has lost its status. Laurence J. Peter |
|
BACK IN BLACK WITH THIS CLASSIC CYBERBARF T-SHIRT!
FEATURING: THE REAL NEWS IMPACT EDITORIAL CARTOONS WRIGLEYVILLE WAR POLITICS ENDORPHIN RUSH THE DARK ABYSS RANDOM ELECTRONS SPECIALS
FEATURING: THE REAL NEWS ARCHIVES CARTOONS MADAME'S TEA HOUSE THE BAR EXPLORE THE CITY SCAPE UNDER CONSTRUCTION SURPRISES ESTORE SPECIALS |
cyberbarf
THE STEAM PUNK SPECIAL EDITION featured new Music from Chicago Ski & the (audio) Real News: (mp3/4:14 length)
EXAMINING THE NET WAY OF LIFE cyberbarf™ distributed by pindermedia.com, inc.
|
cyberbarf
Distribution ©2001-2013 pindermedia.com, inc.
All Ski graphics, designs, cartoons and images copyrighted.
All Rights Reserved Worldwide.