cyberbarf
EXAMINE THE NET WAY OF LIFE
Data Profiling
A woman in suburban Chicago has not used her credit card in one year. Within one day of a charge in Missouri, her credit card company notifies her of a suspicious transaction on her account for a store charge of $340. Not a lot of money. One transaction in hundred of thousands of credit card swipes that day. But swipe it was. She did not make that purchase. The credit card company was right in its suspicion that someone had misappropriated her account number and fraudulently attempted to take money and/or property from a shopkeeper. But credit card companies have to be sophisticated to this kind of fraud. Or the entire credit card system would fail for lack of trustworthiness. Then we all would be doomed.
The suspicious transaction could take variable forms. The sudden use of a dormant credit card could raise a red flag. The comparison of shop zip code to account holder zip code could raise a red flag. The type and size of the transaction in comparison to past purchases could raise a red flag. Wait, past buying behavior?
You must be aware that your credit card company has compiled a digital fingerprint of all your past purchases in its data bases. It can extract personality traits, buying habits, and track your movements like a professional hunter stalking its wild game in the forest. Yes, every person in America with a piece of plastic in their wallet has a digital data profile.
It was what privacy advocates fear. It is what telemarketers and sales associates will buy. The data mining of personal financial information to create individual specific sales pitches is the new gold standard in the service economy.
It is like you have a private detective trailing your every movement. Where you went (gas, hotel, restaurant receipts), where you shop (grocer, department stores), and what you bought (food, clothes). Every piece of your transactional life is now documented since we all use credit cards as the primary means of payment.
For the big spenders, there is more junk mail. It used to be that you had to apply for a credit card. American Express used to be difficult to obtain because of its credit policies and unlimited monthly charge limits. But that has changed for the worse. After data mining, credit card issuers send on average at least one credit card to you a week in the mail. You are PRE APPROVED for a new piece of plastic! One man took all these offers and became a millionaire-- a person who owed more than a million dollars in credit card debt. Credit card issuers love people who use credit cards because they need the high interest rate on the balances and charge service fees for cash flow.
Data profiling is also a tool for law enforcement to trace crime suspects. If a suspect has an alibi, then detectives can get confirmation of that story by tracing his payment history during the relevant date and time period. It is circumstantial evidence of both guilt and innocence, depending on which side of the argument you are on.
Mining in the traditional sense is dangerous and back-breaking. During the California gold rush of 1850s, men made their fortune or died broke. Boom or bust. Data mining is really no different. There was a boom time that lead to all of this telemarketing, floods of junk mail, and unsolicited offers. But the backlash has occurred: the do not call list sponsored by the federal government was a response to the intrusions of the telemarketing industry. It will pull back the more public disclosures of data mining, but it will not stop data profiling.
Ski's Pocket Staple Remover
The battle over intellectual property rages on in the technology community. SCO is suing IBM over the alleged incorporation of proprietary UNIX code in a new version of enterprise Linux software. The battles over the right to patent universal computer operations, like one click commands, for ecommerce applications, still boggles the average person's mind. In some sense, things seem to be getting out of hand.
At the same time, there is a part of me that has the notion of being a Renaissance Man. Back in the day, men were supposed to be self-sufficient, clever, mechanically inclined and independent. Multitasking in the middle ages was another word for survival. Even early American great men were inventors, authors, intellectuals, scientists-- the likes of Ben Franklin and electricity, or Thomas Jefferson's quest for knowledge, or even Mark Twain, who received patents for an invention. We all had the opportunity to be Renaissance men (or women). Throughout school, we were given a wide range of subjects to study and master. Biology, mathematics, art, science, literature/writing. But when this elementary education skill set was completed, we were narrowed into secondary education specialization towards majors, degrees, and finally, a specialized career skill path.
pinderWear Tees on Sale Now!!!!
Patents are the methodology to stake one's claim on an invention. The reward is the opportunity to exploit the permanent manifestation of the idea for a short term monopoly. The patent process is a complex, technical and expensive exercise in notifying the world of your great ideas. In one brief moment, the above world of technology invention, the silliness of missing a simple tool, and being a self-reliant fixer came together.
Around the office copier, the metal staple removers are always missing. They wander away more often than nomads. It is frustrating to bounce from desk to desk in search of this simple jaw-like tool to unbind a set of paper pages. Out of this daily frustration came one of those fits of inspirational problem solving transformed herein to Ski's Patented Pocket Staple Remover:
SKI'S POCKET STAPLE REMOVER
INVENTOR: P.C. Pinderski
BACKGROUND OF INVENTION: One of the most frustrating things around the copy machine is the fact that there is never a conventional stapler remover. Metal staple removers get lost more often than not in an office environment. The sharp points and size and configuration make it uncomfortable to carry one in a pocket like a comb. When a worker is in a hurry to make copies for a client or a project deadline, time is wasted trying to find a staple remover to lift out the stapled papers in order to document feed into the copier. In one of those hurried moments of not being able to find a conventional metal tooth spring loaded staple eaters, I had to come to a quick solution. So I took out my wallet, and extracted a credit card.
OBJECTS AND STATEMENT OF INVENTION: The object of the invention is a portable, personal, staple remover that can be easily carried in a person's pocket, or wallet. The statement of the invention is that a flat, plastic card can act as an effective means of removing staple from clamped papers.
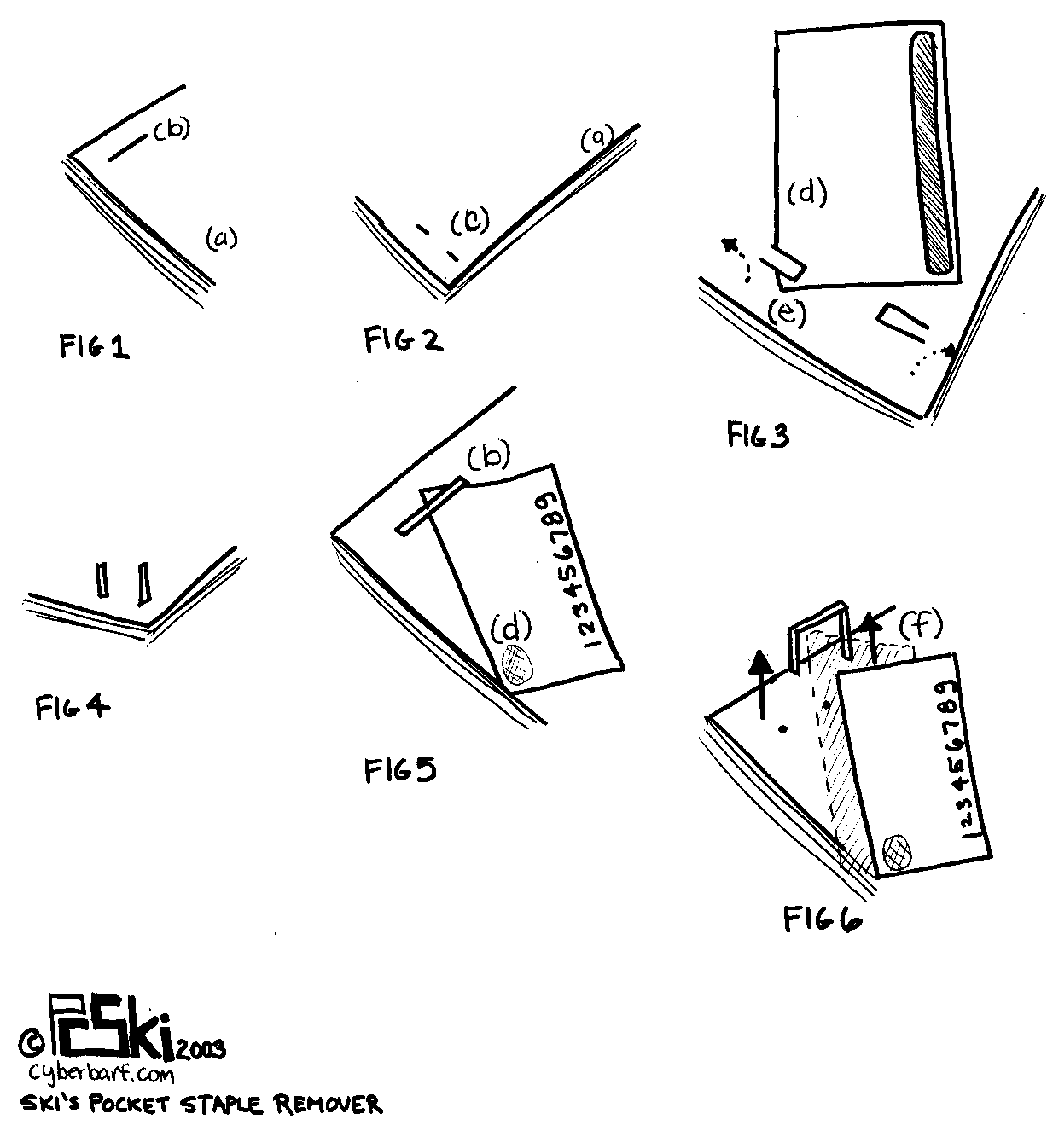
BRIEF DESCRIPTION OF DRAWINGS: The following drawing is described as follows:
Figure 1 represents the corner of a stapled document, defined as individual sheets of two or more paperius materials (Fig 1 (a)) bound together with a metal fastner commonly known as a staple (Fig 1 (b)).
Figure 2 represents the backside of a stapled document, defined as individual sheets of two or more paperious materials (Fig 2(a)) with the backside configuration of the staple points that have been flattened in order to secure the paper sheets together (Fig 2 (c)).
Figure 3 represents the invention of the insertion (Fig 3 (e)) of a thin, flat, piece of plastic, or other flexible but strong material, (Fig 3 (d)), underneath the flattened staple points (Fig 3(e)) so as Fig 3(d) is situated between the document page (Fig 2(a)) and the flattened staple points (Fig 2 (c)). Once the invention material (Fig 3 (d)) is inserted, the arrows represent the lift motion of the invention material (Fig 3 (d)) in an upward and outward movement to raise the staple point (Fig 2(c)) to a 90 degree angle with the document page surface (Fig 2 (a)).
Figure 4 represents the completion of the mechanical operation described in the above paragraph showing the staple points now in a 90 degree position in relation to the document sheet page surface.
Figure 5 represents the next operation of the invention material. After turning the document over to its front page, the invention material (Fig 5(d)) is inserted under the flat portion of the staple (Fig 5 (b)).
Figure 6 represents the mechanics of the invention after the invention material is inserted in a position between the staple (Fig 1(b)) and surface of the document page (Fig 1(a)) of lifting directly upward with such sufficient force as to correspondingly lift the staple from its position through the document pages as represented in Fig 6 (f)).
CLAIMS: Inventor claims that the use of a thin, flat piece of plastic as a device for the removal of staples from secured documents is an effective, efficient and resourceful method different than the conventional metal claw and spring devices. Inventor claims that the utilitarian difference between the conventional removal of a staple with a metal claw and spring device is that the inventor's thin, flat plastic card approach is an easily portable staple remover as it can easily and comfortably be carried in a person's pocket or wallet without discomfort. The ability to carry one of the Inventor's portable staple removers creates greater efficiency in the removal of staples from documents since the person has his or her own removal device always at hand. Inventor claims that this (credit card) method works just as well as a conventional staple remover.
Try it. Maybe you will like it. It may save some gray hairs or cursing in crunch time. It is a simple idea, and a search of the patent database showed no similar idea application. Others may have used it. The idea itself is patentable per se, because a simple notion with readily available plastic cards has no enforcement of a little circle R symbol since every single man, woman and child in America already has the device on them since each his or her own credit card. But in the computer tech industry, it does not stop firms from claiming one click commerce, the look-and-fee of a computer screen, or other standardized functions as proprietary property. Maybe this is my statement against those types of tech range wars. The above solution for a nagging office problem is published in the public domain as an antithesis to those other technology proprietors claiming standard functions as patentable ideas.
Bends & Trends
Hackers of Old
The term HACKER has a slightly different meaning depending on your age.
A hack once described a person hired to do routine, often dull, literary drudge. It also meant a person who had a carriage or horse for hire. It was updated in the American vocabulary to describe the act of driving a taxicab. In a general old world sense, a hacker is a person ready for hire, in reserve to do routine or dull tasks for others.
A computer hacker is a modern version of the hack waiting for something to do. Boredom leads to the mind wandering. Mind wandering leads to day dreaming. Day dreaming leads to more boredom. Extreme boredom leads to petty vandalism. Petty vandalism leads to bigger thrills; felony vandalism.
A computer hacker with too much idle time on his hands is the devil in his own workshop. On the other side of the coin, an employed hacker on the time clock, is called a computer programmer, whose services command premium wages from his employer to prevent his counterpart from screwing up the enterprise system. Soul brothers or sole brothers? If you put them side by side in a police line-up, it would probably be hard to tell them a part from each other.
Some of the early and brilliant hackers that got caught, found a lucrative way to keep in the game: they became big money computer security consultants. They used their acquired knowledge base of hacking to creative a marketable skill to thwart the next generation of hackers. In an odd way, it was the first unconnected peer on peer network struggle.
A cab driver will tell you he meets all kinds of people. A computer hacker will probably tell you that he meets all kinds of kindred spirits in secret chatrooms, code sharing conventions and the gamer's room of the local seedy motel.
Now, the purist will argue that hackers provide a function like pesky insects, rodents and other creatures of a set ecology. Hackers are a force like nature that demands the normal computer programmers to be ready to adapt their code, update their security, and refine their programs to be better and better. It is like an outside consultant yelling at the R & D department to get a move on. The problem is the real R & D Department is a division of the FBI which takes the cyberassault on corporate computers very seriously. Corporate CEOs have told the bureau that they lose millions each time their system goes down during one of these virus attacks. Lost time is lost money. Lost money is lost tax dollars. Lost tax dollars mean bigger deficits. And lost campaign donations to the politicians. Who wants to be an unemployed politician in this economy? Exactly, they do not want to end up like a 20 year old sitting in his parent's house eating donuts and overcaffeinated soft drinks all day while writing lines of code to get back at people who let them down in the past?
T-shirts, Caps, Mugs. Check for Specials!
Rocky, the unpaid tech support department for cyberbarf.com, was in a bad mood a while back. So he decided to give me a good natured site rib. He sent me this screen shot he created:
Look familiar? It is the August, 2003 cyberbarf issue translated. Now, I realize some people may not understand everything I am trying to say here, but this regurgitation is kinda funny. Kudos.
HEY WEB SURFERS!
NEW!
SURF TO LIVE
LIVE TO SURF (tee)
NEW SPECIAL
T-SHIRTS ON SALE
AT THE PINDERMEDIA.COM STORE
Also available the Net Addict! t-shirt.
Your support keeps this Site moving forward. Thank you!
Distribution ©2001-2003 pindermedia.com, inc.
All Rights Reserved Worldwide.
Contact Information
Terms and Conditions
Trademarks
Archives